- How To Use Driver Verifier
- How To Access Driver Verifier Manager In Windows 10
- Driver Verifier Manager Windows 10 7
- Driver Verifier Manager Windows 10 Download
- Microsoft Verified Apps Disable
Windows has, what is called as, Driver Verifier Manager. It’s a very useful tool to identify problematic drivers. To open it type verifier in start menu search box and hit enter. Windows includes a “Driver Verifier” tool that can stress test your device drivers. It detects bad driver behavior, but any issue found triggers an immediate blue screen of death. Most PC users should stay away. This utility has been around since Windows 2000 and XP, and it’s still part of Windows 10 today. Nov 20, 2015 Windows has, what is called as, Driver Verifier Manager. It’s a very useful tool to identify problematic drivers. To open it type verifier in start menu search box and hit enter.
I am trying to disable the Windows 10 driver signature verifier.
This is causing constant BSOD errors - all showing 'Driver Verifier IOManger Violation'
I am trying to install an old video driver. I would like to completely disable the verifier program, but so far I can't.
I have spent the last few days researching and trying every variation of the following strategies
I rebooted into advanced setup options
in cmd.exe
I then hit F7 to disable driver signature verification
I opened gpedit.msc
Enabled the option for code signed drivers
Enabled Test Mode
I tried to disable any video drivers in use under device manager, but there are no video drivers installed at all.
In cmd.exe I ran 'verifier' to open the driver verifier manager
I choose 'Display existing settings'
All options read as 'no'
I set compatibility mode on my driver install package and am running as administrator
After every install attempt the BSOD screen appears with the driver verifier error message.
Suggestions?
fixer12343 Answers
the verifier settings are stored in the registry under HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession ManagerMemory ManagementVerifyDrivers and HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession ManagerMemory ManagementVerifyDriverLevel. Delete both entries to get rid of Driver Verifier.
I'm going to leave this here for anyone who has the same problem I did:
- Click on 'See advanced repair options'
- Go to 'Troubleshoot'
- Tap on 'Advanced Options'
- Click on 'Start-up Settings'
- Press 4 to start up in safe mode
- Once you're logged in, type
run - Type
verifier.exe - Click 'delete existing settings'
- Go to the start menu and click 'restart'
Hope this helps. I was in a frustrating loop where NOTHING was disabling driver verifier, but this worked for me, so I hope it does for you too.
To expand on MagicAndre's answer. A bit of more generic info to help those who don't know how to access a non-default registry hive and/or may not see their drive in recovery mode (like my PCIe SSD, for example)
If you can't see Startup Options in your recovery mode, your Recovery partition might not be able to see your SSD drive. To check this, try opening the recovery command prompt. Once there, type diskpart and then list disk when the diskpart prompt appears. If you see the disk that matches your OS drive, then you can simply open regedit from the command prompt.
In regedit
How To Use Driver Verifier
- Select HKEY LOCAL MACHINE and then hit
File : Load Hive - Navigate to your OS Drive, then open WindowsSystem32ConfigSYSTEM (no file extension), give the hive a temporary name (e.g. CDRIVESYSTEM)
- Navigate through registry -
HKLMCDRIVESYSTEMCurrentControlSetControlSESSION MANAGERMEMORY MANAGEMENTVerifyDrivers - Remove
VerifyDriverLevelandVerifyDriversvalues - Hit
File : Unload Hive - Restart your machine. With any luck you'll stop crashing on OS boot!
How To Access Driver Verifier Manager In Windows 10
Can't see drive
If you can't see your OS drive there, you can try creating a bootable USB stick with WinPE installed on it. Booting into WinPE may allow your disk to appear in diskpart, in which case you can follow the regedit steps above to remove the verifier values fromHKLMSystemCurrentControlSetControlSESSION MANAGERMEMORY MANAGEMENT
protected by Twisty ImpersonatorJan 5 at 12:17
Thank you for your interest in this question. Because it has attracted low-quality or spam answers that had to be removed, posting an answer now requires 10 reputation on this site (the association bonus does not count).
Would you like to answer one of these unanswered questions instead?
Not the answer you're looking for? Browse other questions tagged windowswindows-10driversbsodmicrosoft-driver-verifier or ask your own question.
-->Driver Verifier monitors Windows kernel-mode drivers and graphics drivers to detect illegal function calls or actions that might corrupt the system. Driver Verifier can subject Windows drivers to a variety of stresses and tests to find improper behavior. You can configure which tests to run, which allows you to put a driver through heavy stress loads or through more streamlined testing. You can also run Driver Verifier on multiple drivers simultaneously, or on one driver at a time.
Caution
- Running Driver Verifier could cause the computer to crash.
- You should only run Driver Verifier on computers that you are using for testing and debugging.
- You must be in the Administrators group on the computer to use Driver Verifier.
- Driver Verifier is not included in Windows 10 S, so we recommend testing driver behavior on Windows 10 instead.
Where can I download Driver Verifier?
You don't need to download Driver Verifier, because it is included with most versions of Windows in %WinDir%system32 as Verifier.exe. (Driver Verifier is not included with Windows 10 S.) Driver Verifier is not distributed separately as a download package.
For information about changes in Driver Verifier for Windows 10 and previous versions of Windows, see Driver Verifier: What's New.
When to use Driver Verifier
Run Driver Verifier throughout development and testing of your driver. More specifically, use Driver Verifier for the following purposes:
To find problems early in the development cycle, when they are easier and less costly to correct.
For troubleshooting and debugging test failures and computer crashes.
To monitor behavior when you deploy a driver for testing using the WDK, Visual Studio, and the tests from the Windows Hardware Lab Kit (Windows HLK) or Windows Hardware Certification Kit (for Windows 8.1). For more information about testing drivers, see Testing a Driver.
How to start Driver Verifier
You should only run Driver Verifier on test computers, or on computers that you are testing and debugging. To get the most benefit from Driver Verifier, you should use a kernel debugger and connect to the test computer. For more information about debugging tools, see Debugging Tools for Windows (WinDbg, KD, CDB, NTSD).
Start a Command Prompt window by selecting Run as administrator, and type verifier to open Driver Verifier Manager.
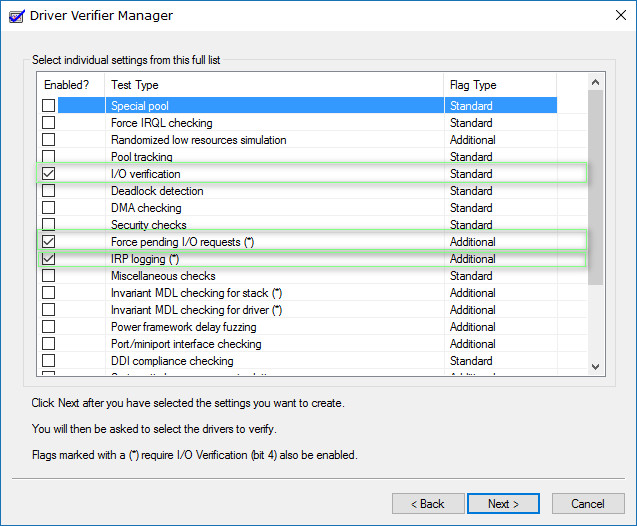
Select Create standard settings (the default task), and click Next.
You can also choose Create custom settings to select from predefined settings, or to select individual options. For more information, see Driver Verifier options and rule classes and Selecting Driver Verifier Options.
Under Select what drivers to verify, choose one of the selection schemes described in the following table.
Option Recommended use Automatically select unsigned drivers Useful for testing on computers that are running versions of Windows that do not require signed drivers.
Automatically select drivers built for older versions of Windows Useful for testing driver compatibility with newer versions of Windows.
Automatically select all drivers installed on this computer Provides maximum coverage in terms of the number of drivers that are tested on a system. This option is useful for test scenarios where a driver can interact with other devices or drivers on a system.
This option can also exhaust the resources available for Special Pool and some resource tracking. Testing all drivers can also adversely affect system performance.
Select driver names from a list In most cases, you will want to specify which drivers to test.
Selecting all drivers in a device stack allows the Enhanced I/O Verification option to track objects and check compliance because an I/O request packet (IRP) is passed between each of the drivers in the stack, which allows for a greater level of detail to be provided when an error is detected.
Select a single driver if you are running a test scenario that measures system or driver performance metrics, or if you want to allocate the greatest number of resources available for detecting memory corruption or resource tracking issues (such as deadlocks or mutexes). The Special Pool and I/O Verification options are more effective when used on one driver at a time.
If you chose Select driver names from a list, click Next, and then select one or more specific drivers.
Click Finish, and then restart the computer.
Note
You can also run Driver Verifier in a Command Prompt window without starting Driver Verifier Manager. For example, to run Driver Verifier with the standard settings on a driver called myDriver.sys, you would use the following command:
For more information about command line options, see Driver Verifier Command Syntax.
How to control Driver Verifier
You can use either Driver Verifier Manager or a command line to control Driver Verifier. To start Driver Verifier Manager, see How to start Driver Verifier, earlier in this topic.
For each of the following actions, you can use Driver Verifier Manager or enter a command line.
To stop or reset Driver Verifier
In Driver Verifier Manager, select Delete existing settings, and then click Finish.
or
Enter the following command at a command prompt:
Restart the computer.
To view Driver Verifier statistics
In Driver Verifier Manager, select Display information about the currently verified drivers, and then click Next. Continuing to click Next displays additional information.
or
Enter the following command at a command prompt:
To view Driver Verifier settings
Driver Verifier Manager Windows 10 7
In Driver Verifier Manager, select Display existing settings, and then click Next.
or
Enter the following command at a command prompt:
How to debug Driver Verifier violations
To get the most benefit from Driver Verifier, you should use a kernel debugger and connect it to the test computer. For an overview of debugging tools for Windows, see Debugging Tools for Windows (WinDbg, KD, CDB, NTSD).
If Driver Verifier detects a violation, it generates a bug check to stop the computer. This is to provide you with the most information possible for debugging the issue. When you have a kernel debugger connected to a test computer that is running Driver Verifier, and Driver Verifier detects a violation, Windows breaks into the debugger and displays a brief description of the error.
All violations detected by Driver Verifier result in bug checks. Common bug check codes include the following:
For more information, see Handling a Bug Check When Driver Verifier is Enabled. For tips about debugging Bug Check 0xC4, see Debugging Bug Check 0xC4: DRIVER_VERIFIER_DETECTED_VIOLATION.
Driver Verifier Manager Windows 10 Download
When you start a new debugging session, use the debugger extension command, !analyze. In kernel mode, the !analyze command displays information about the most recent bug check. To display additional information, to help identify the faulting driver, add option -v to the command at the kd> prompt:
In addition to !analyze, you can enter the following debugger extensions at the kd> prompt to view information that is specific to Driver Verifier:
!verifier dumps captured Driver Verifier statistics. Use !verifier -? to display all of the available options.
!deadlock displays information related to locks or objects tracked by Driver Verifier's deadlock detection feature. Use !deadlock -? to display all of the available options.
!iovirp [address] displays information related to an IRP tracked by I/O Verifier. For example:
!ruleinfo [RuleID] displays information related to the DDI compliance checking rule that was violated. (RuleID is always the first argument to the bug check.) All rule IDs from DDI compliance checking are in the form 0x200nn. For example: